Okay,
another prevalent virus named Win32.downloader.gen hit the computers more
severely these months. Win32.downloader.gen is a malicious threat found since
March, but up to now, there are still many victim users seeking for help to
remove this stuff. A post from a community goes like this: My brother got a
virus on his computer called Win32.downloader.gen. He has tried repeatedly AVG,
MBAM, and Spybot and none of them can remove this virus. What should we do?
More Win32.downloader.gen related posts are found these months on different
forums or communities of Antivirus programs, such as Spybot, MalwareBytes or
Norton, etc. Do you also encounter the same problem that your Antivirus program
can not get rid of Win32.downloader.gen infection off your computer? Well,
let’s read more information about why Win32.downloader.gen is so malicious and
stubborn and how to remove it with effective manual solution here - the
earliest professional post about Win32.downloader.gen removal published on the
very early March, 2013:
http://blog.teesupport.com/way-to-remove-win32-downloader-gen-virus-removal-tips/
2013年10月30日星期三
How to Stop http://ww6.btosjs.info/ Redirection? Remove http://ww6.btosjs.info/ Completely from PC!
Recently,
one more browser hijacker named http://ww6.btosjs.info/ appears over the cyber network. Many victim computer users are looking for
effective removal solution to get rid of http://ww6.btosjs.info/
hijacker virus completely. You can easily find some posts via different tech
forums or communities asking for assistance. A post on Yahoo! States like this:
My Computer Has The ww6.btosjs.info Virus? What can I do? It doesn't let me go
to any page on the web because it keeps redirecting me to the site I listed.
Can I get an anti virus protection to delete the virus? What are my options?
2013年10月21日星期一
Delete and Remove HEUR.Exploit.Java.CVE-2013-2423.gen Infection - Removal Help
Having
difficulties to get rid of HEUR.Exploit.Java.CVE-2013-2423.gen infection? Does
the Trojan cause multiple issues on the target computer? Worrying about saved
work and net-banking details since the Trojan refused to go no matter how many
times you tried? This post and Tee Support online tech support team will help
you out safely and quickly.
HEUR.Exploit.Java.CVE-2013-2423.gen Information
HEUR.Exploit.Java.CVE-2013-2423.gen
is a file diagnosis for a Windows component, mswsock.dll to be specific, that
has been ''patched'' by the Trojan. Such gadget is applied to sabotage the
infected system while preventing from being spotted and deleted. Users usually
acquire this malware by unwittingly browsing compromised websites or unwarily
downloading pirated application with a security-flawed system.
 HEUR.Exploit.Java.CVE-2013-2423.gen
has multiple purposes depending on the nature of the Trojan and configuration
by the remote attacker. Once upon the successful penetration, the Trojan will
amend system in a way that it can be activated once Windows gets loaded. It may
keep in touch with remote server to fetch other components and update itself
too. HEUR.Exploit.Java.CVE-2013-2423.gen
is also bind with a rootkit Trojan, which makes it hidden from antivirus
program. Indeed, this threat can end certain processes so as to terminate
security services in the vulnerable system. Hence it provides green light for
unauthorized access to the system and other cyber bugs.
HEUR.Exploit.Java.CVE-2013-2423.gen
has multiple purposes depending on the nature of the Trojan and configuration
by the remote attacker. Once upon the successful penetration, the Trojan will
amend system in a way that it can be activated once Windows gets loaded. It may
keep in touch with remote server to fetch other components and update itself
too. HEUR.Exploit.Java.CVE-2013-2423.gen
is also bind with a rootkit Trojan, which makes it hidden from antivirus
program. Indeed, this threat can end certain processes so as to terminate
security services in the vulnerable system. Hence it provides green light for
unauthorized access to the system and other cyber bugs.
The
most dangerous part lies in it payload to gather confidential data and save
them as log file before sending out to remote server which prepared the ground
for possible identity theft and ransom virus launch. In order to prevent
further damage, users should get rid of HEUR.Exploit.Java.CVE-2013-2423.gen as
early as possible.
How to Delete Worm:MSIL/Necast.D Infection? Worm:MSIL/Necast.D Removal Tips
Worm:MSIL/Necast.D Infection
Actually Worm:MSIL/Necast.D is an old infection discovered in November, 2012. Has
Worm:MSIL/Necast.D been stayed on your computer for a long time? How do your
remove Worm:MSIL/Necast.D? Every method has been tried but it is still reported
by antivirus software? It will be easily for you to walk through with
Worm:MSIL/Necast.D virus with this step-by-step guide. If you have any trouble
with the removal process, please feel free to contact Tee Support agents 24/7online for help.
Worm:MSIL/Necast.D Description
Worm:MSIL/Necast.D
is a malicious Trojan horse which is always associated with Java Script
programs. Computer may have been installed with this virus while doing an
update for Java programs or downloading Java applications from unreliable
websites. It is a virus responsible for resulting computer into serious
dangers. Anyhow, the final intention for the appearance of Worm:MSIL/Necast.D
is to compromise the computer vulnerably for cyber criminal attacks.
 Once
the virus is installed, a range of malicious activities will be dropped into
computer to degrade down the security level of your PC. It will conceal itself
in the background, furtively reset system settings, penetrate registry entry
with malicious keys to have it activated automatically with the Windows.
Computer utility will be seriously affected, which makes operation system
performs sluggishly and weirdly. What's more, Worm:MSIL/Necast.D is also
carried with the codes, which can be used to open security leaks for allowing
other infections to infiltrate into computer to push computer even useless in
response. The last but not the least, Worm:MSIL/Necast.D is able to collect
user's sensitive information to online hackers who is evil to rip off money
from user's online account for gaining illegal benefits. Thus, to guarantee for
the security of computer's security and personal rights, Worm:MSIL/Necast.D
should be removed rapidly from the time it is detected.
Once
the virus is installed, a range of malicious activities will be dropped into
computer to degrade down the security level of your PC. It will conceal itself
in the background, furtively reset system settings, penetrate registry entry
with malicious keys to have it activated automatically with the Windows.
Computer utility will be seriously affected, which makes operation system
performs sluggishly and weirdly. What's more, Worm:MSIL/Necast.D is also
carried with the codes, which can be used to open security leaks for allowing
other infections to infiltrate into computer to push computer even useless in
response. The last but not the least, Worm:MSIL/Necast.D is able to collect
user's sensitive information to online hackers who is evil to rip off money
from user's online account for gaining illegal benefits. Thus, to guarantee for
the security of computer's security and personal rights, Worm:MSIL/Necast.D
should be removed rapidly from the time it is detected.Worm:MSIL/Necast.D Has such Dangerous Symptoms
- Worm:MSIL/Necast.D is a nasty worm parasite
- Worm:MSIL/Necast.D may show fake security & messages
- Worm:MSIL/Necast.D may display numerous annoying advertisements
- Worm:MSIL/Necast.D may be controlled by a remote person
- Worm:MSIL/Necast.D may come with additional spyware
- Worm:MSIL/Necast.D violates your privacy and compromises your security
Infected by Trojan Horse generic29 AHHS? How to Remove Trojan generic29 AHHS
Is
your computer bogged down due to Trojan horse generic29 AHHS infection? Does
your computer get infected with Trojan Horse Generic29.AHHS but the antivirus
program in the computer cannot remove it? You are not alone as the one who is
struggling to get rid of Trojan horse generic29 AHHS but coming to no avail.
You may get help here with Tee Support online research and tech support team.
 See
how do people look for solutions over the Internet to terminate this malicious
Trojan on various forums or communities.
See
how do people look for solutions over the Internet to terminate this malicious
Trojan on various forums or communities.
Just
caught the virus called Trojan Horse Generic29.AHHS. The AVG detects it but
cannot remove (access denied.) …
Trojan
Horse Generic29.AHHS zero access rootkit… Aug
13, 2013
Trojan
Horse Generic29.AJGE virus problem - Am I infected ... Jun 4, 2013
Well,
first of all, let’s see ------
What Is Trojan horse generic29 AHHS?
Trojan
horse generic29 AHHS is a combination of worm and Trojan that is created to
corrupt the target system and gather confidential information from it. The
Trojan can also add more malware on the ailing PC, downloading them from a
remote location with its backdoor function. A startup registry will be added to
guarantee an automatic start-up as soon as Windows gets loaded. In order to get
all payload carried out without any obstacles, Trojan generic29 AHHS will make
some changes on the registry so that it can bypass Windows firewall. Besides,
the worm has self-replicating function which may be the culprit of a severely
lagged response with serious system resource drains.
Other
malicious actions which are configured by the Trojan author will be performed
singly or simultaneously as but not limited to below:
2013年9月30日星期一
Uninstall / Remove Antivirus Security Pro Rogue off Your Computer Completely
AntivirusSecurity Pro is another piece of MultiRogue 2013 which is designed and
developed to fool average computer users into purchasing the license key of
Antivirus Security Pro - the bogus software. By bombarding the infected system
with multiple fake security warnings, the rogue tried every shift available to
convince users of a severely contaminated machine. You may be warned here and
there that the computer is infected with high risk malware, it even states your
Chrome.exe, or eplorer.exe is infected with a risky Trojan. Besides, fake
Antivirus Security Pro Firewall alert or similar alert comes up when you try to
open a program.
There
are also numerous occasions that it generates an automatic system scan and
reports multiple threats in the wake of the scan. What's more, It makes
operating system registry modification to make the computer unusable. It then
trumpets that the activation of Antivirus Security Pro is able to get all
fixed. It's believed to be a waste of money to pay for a worthless full version
which is created with no virus dictionary and in a position to fixing nothing.
Other than any infection displayed by Antivirus Security Pro, the scam is the
only threats you need to remove, the sooner the better.
Antivirus
Security Pro Screenshot

How to Remove Trojan PUP.Optional.4Squared Infection Completely? PUP.Optional.4Squared Removal Guide
Severe
Trojan infection PUP.Optional.4Squared attacks this month and has compromised
more and more computers. Are you seeking for an available way to remove Trojan
PUP.Optional.4Squared out from your computer? Ways have been tried but all
failed? You can give a shot on the removal process as below. If you are still
confused with the process, please feel free to contact Tee Support agents 24/7
online for further detailed instructions.
Symptoms of Trojan PUP.Optional.4Squared
- Trojan PUP.Optional.4Squared is a nasty Trojan parasite
- Trojan PUP.Optional.4Squared may show fake security & messages
- Trojan PUP.Optional.4Squared may display numerous annoying advertisements
- Trojan PUP.Optional.4Squared may be controlled by a remote person
- Trojan PUP.Optional.4Squared may come with additional spyware
- Trojan PUP.Optional.4Squared violates your privacy and compromises your security
2013年9月12日星期四
Antivirus Program Cannot Remove Worm:win32/Boberog.AZ? Manual Removal Help Here
Constantly
Receiving security alert of Worm:win32/Boberog.AZ virus from the security tool
and have no idea to get rid of it completely? This manual removal guide will
help you remove Worm:win32/Boberog.AZ easily and quickly. If the issue to your
computer still can't be solved, you're welcome to contact Tee Support agents
24/7 online for more detailed instructions.
What is Worm:win32/Boberog.AZ?
Worm:win32/Boberog.AZ
is a perilous Trojan horse which will bring computer with diverse damages for
leading computer to dangerous situation. As an offensive virus, it is attempted
to severely degrade down computer security defense so as to add system with malicious
codes and give rise to lots of destruction. Once infected, it can locate into
the essential part of system, penetrating registry entry with sub-key to have
it started automatically together with the Windows. It will totally mess up
system settings and slow down network speed. You will be unwillingly popped up
with advertisements or redirected to various websites which are promoted for
commercial profits. What's more, Worm:win32/Boberog.AZ is capable to keep
connecting with remote servers to bring in many other severe infections via the
backdoor it creates on the background of system. It is tended to collect and
send the stolen information to remote hackers for making illicit benefits from
your account. Summing up, Worm:win32/Boberog.AZ infiltrates into computer
aggressively and causes various problems that it is suggested to get rid of it
as rapidly as you can.

2013年9月11日星期三
Trojan.zaccess Infection Removal - How to Delete Trojan.zaccess with Manual Removal Means
Trojan.zaccess is a type of Trojan prevalent
these days and has compromised more and more computers. Trojan.zaccess should
be removed if detected. Is your computer attacked by Trojan.zaccess? Having
tried several means on its removal but making no progress? This post and Tee
Support online tech support team will help find the solution.
Trojan.zaccess Analysis
Actually, Trojan.zaccess has some similar
features like other vicious Trojans, such as ojan.Zeroaccess, Win32:ZAccess-PB, Trojan/ZAccess-BS, Trojan.Win32.ZAccess.ca (v). Trojan.zaccess is a
variant from a huge Trojan clan that shares the same purpose and mechanism but
it has minimal difference in affecting the target system. In most instances,
the Trojan sneaks into the computer and completes the unauthorized installation
through various security exploits. Following it will make several adjustments
that is crucial to carry out its tasks. This malware is created to collect
sensitive credentials and distribute other infection. A backdoor function is
added to allow remote hackers to monitor the vulnerable system. Not only will
the Trojan compromise your credit card, netbanking details, etc, but also the
computer security system will be severely degraded until it becomes
defenseless. Thus users should get rid of Trojan.zaccess once upon the
detection.
2013年9月4日星期三
Can not Remove Trojan Generic34.YQE Virus? Trojan Generic34.YQE Manual Removal Help
How much do you know about TrojanGeneric34.YQE virus? Why can't it be removed by security programs thoroughly?
What's the best way to delete it once for all? It will be easily for you to
walk through with Trojan Generic34.YQE virus with this step-by-step guide. If
you have any trouble with the removal process, please feel free to contact Tee
Support agents 24/7 online for help.
Trojan Generic34.YQE Is an Undoubted Terrible Virus by Impression
- Trojan Generic34.YQE is a nasty Trojan parasite
- Trojan Generic34.YQE may show fake security messages
- Trojan Generic34.YQE may display numerous annoying advertisements
- Trojan Generic34.YQE may come with additional spyware
- Trojan Generic34.YQE violates your privacy and compromises your security

How to Get Rid of PUP.Optional.Wajam.A Completely - PUP.Optional.Wajam.A Removal Help
Are you seriously mad with
PUP.Optional.Wajam.A virus as it always turns up again after having it removed
by security programs? What's the best solution to exterminate it permanently?
If there is no solution to help you availably, this step-by-step guide will
help remove PUP.Optional.Wajam.A easily. Once there is any problem during the
removal process, please contact Tee Support agents 24/7 online for more
detailed instructions with the expert.
The Lists of Symptoms about PUP.Optional.Wajam.A
- PUP.Optional.Wajam.A is a dangerous Trojan parasite
- PUP.Optional.Wajam.A may show fake security messages
- PUP.Optional.Wajam.A may display numerous annoying advertisements
- PUP.Optional.Wajam.A may be controlled by a remote person
- PUP.Optional.Wajam.A may come with additional spyware
- PUP.Optional.Wajam.A violates your privacy and compromises your security

2013年4月8日星期一
Trojan alureon removal guide - How to remove Trojan alureon Infection?
Constantly receiving security alert of Trojan alureon from the security tool and have no idea to get rid of it completely? This manual removal guide will help you remove Trojan alureon easily and quickly. If the issue to your computer still can't be solved, you're welcome to contact Tee Support agents 24/7 online for more detailed instructions.
 Trojan alureon is a kind of perilous Trojan horse which will bring computer with diverse damages for leading computer to dangerous situation. As an offensive virus, it is attempted to severely degrade down computer security defense so as to add system with malicious codes and give rise to lots of destruction. Once infected, it can locate into the essential part of system, penetrating registry entry with sub-key to have it started automatically together with the Windows. It will totally mess up system settings and slow down network speed. You will be unwillingly popped up with advertisements or redirected to various websites which are promoted for commercial profits. What's more, Trojan alureon is capable to keep connecting with remote servers to bring in many other severe infections via the backdoor it creates on the background of system. It is tended to collect and send the stolen information to remote hackers for making illicit benefits from your account. Summing up, Trojan alureon infiltrates into computer aggressively and causes various problems that it is suggested to get rid of it as rapidly as you can.
Trojan alureon is a kind of perilous Trojan horse which will bring computer with diverse damages for leading computer to dangerous situation. As an offensive virus, it is attempted to severely degrade down computer security defense so as to add system with malicious codes and give rise to lots of destruction. Once infected, it can locate into the essential part of system, penetrating registry entry with sub-key to have it started automatically together with the Windows. It will totally mess up system settings and slow down network speed. You will be unwillingly popped up with advertisements or redirected to various websites which are promoted for commercial profits. What's more, Trojan alureon is capable to keep connecting with remote servers to bring in many other severe infections via the backdoor it creates on the background of system. It is tended to collect and send the stolen information to remote hackers for making illicit benefits from your account. Summing up, Trojan alureon infiltrates into computer aggressively and causes various problems that it is suggested to get rid of it as rapidly as you can.
What is Trojan alureon?
 Trojan alureon is a kind of perilous Trojan horse which will bring computer with diverse damages for leading computer to dangerous situation. As an offensive virus, it is attempted to severely degrade down computer security defense so as to add system with malicious codes and give rise to lots of destruction. Once infected, it can locate into the essential part of system, penetrating registry entry with sub-key to have it started automatically together with the Windows. It will totally mess up system settings and slow down network speed. You will be unwillingly popped up with advertisements or redirected to various websites which are promoted for commercial profits. What's more, Trojan alureon is capable to keep connecting with remote servers to bring in many other severe infections via the backdoor it creates on the background of system. It is tended to collect and send the stolen information to remote hackers for making illicit benefits from your account. Summing up, Trojan alureon infiltrates into computer aggressively and causes various problems that it is suggested to get rid of it as rapidly as you can.
Trojan alureon is a kind of perilous Trojan horse which will bring computer with diverse damages for leading computer to dangerous situation. As an offensive virus, it is attempted to severely degrade down computer security defense so as to add system with malicious codes and give rise to lots of destruction. Once infected, it can locate into the essential part of system, penetrating registry entry with sub-key to have it started automatically together with the Windows. It will totally mess up system settings and slow down network speed. You will be unwillingly popped up with advertisements or redirected to various websites which are promoted for commercial profits. What's more, Trojan alureon is capable to keep connecting with remote servers to bring in many other severe infections via the backdoor it creates on the background of system. It is tended to collect and send the stolen information to remote hackers for making illicit benefits from your account. Summing up, Trojan alureon infiltrates into computer aggressively and causes various problems that it is suggested to get rid of it as rapidly as you can.Remove Trojan horse back door generic 15 BYNL Infection - Delete back door generic 15 BYNL Trojan Easily
Is your computer bogged down due to Trojan horse back door generic 15 BYNL infection? It's white-listed and seems to be irreparable. What damage Trojan horse back door generic 15 BYNL may result in and what should you do to deal with such tough Trojan? You may get the answer here with Tee Support online tech support team.
 Trojan horse back door generic 15 BYNL is a pesky Trojan infection that is used to steal important passwords and make the target system more vulnerable. When the Trojan is downloaded from pirate portal such as insalubrious website or questionable program, it will quickly unzip the files and completes the installation. First of all, Trojan horse back door generic 15 BYNL will add itself a start-up entry which makes sure that the program code can execute each time when Windows gets loaded. Other modification will soon be made too that is essential for the carrying out of its payloads. In order to connect to remote server to fetch other components and download other executables, it will change Firewall and other security settings so as to prevent being spotted while there are unauthorized data transfer. It also allows remote hacker to access to and manipulate the system in this way. Whatever the motivation is, it's important for users to completely remove Trojan horse back door generic 15 BYNL as early as possible.
Trojan horse back door generic 15 BYNL is a pesky Trojan infection that is used to steal important passwords and make the target system more vulnerable. When the Trojan is downloaded from pirate portal such as insalubrious website or questionable program, it will quickly unzip the files and completes the installation. First of all, Trojan horse back door generic 15 BYNL will add itself a start-up entry which makes sure that the program code can execute each time when Windows gets loaded. Other modification will soon be made too that is essential for the carrying out of its payloads. In order to connect to remote server to fetch other components and download other executables, it will change Firewall and other security settings so as to prevent being spotted while there are unauthorized data transfer. It also allows remote hacker to access to and manipulate the system in this way. Whatever the motivation is, it's important for users to completely remove Trojan horse back door generic 15 BYNL as early as possible.
Trojan horse back door generic 15 BYNL Analysis
 Trojan horse back door generic 15 BYNL is a pesky Trojan infection that is used to steal important passwords and make the target system more vulnerable. When the Trojan is downloaded from pirate portal such as insalubrious website or questionable program, it will quickly unzip the files and completes the installation. First of all, Trojan horse back door generic 15 BYNL will add itself a start-up entry which makes sure that the program code can execute each time when Windows gets loaded. Other modification will soon be made too that is essential for the carrying out of its payloads. In order to connect to remote server to fetch other components and download other executables, it will change Firewall and other security settings so as to prevent being spotted while there are unauthorized data transfer. It also allows remote hacker to access to and manipulate the system in this way. Whatever the motivation is, it's important for users to completely remove Trojan horse back door generic 15 BYNL as early as possible.
Trojan horse back door generic 15 BYNL is a pesky Trojan infection that is used to steal important passwords and make the target system more vulnerable. When the Trojan is downloaded from pirate portal such as insalubrious website or questionable program, it will quickly unzip the files and completes the installation. First of all, Trojan horse back door generic 15 BYNL will add itself a start-up entry which makes sure that the program code can execute each time when Windows gets loaded. Other modification will soon be made too that is essential for the carrying out of its payloads. In order to connect to remote server to fetch other components and download other executables, it will change Firewall and other security settings so as to prevent being spotted while there are unauthorized data transfer. It also allows remote hacker to access to and manipulate the system in this way. Whatever the motivation is, it's important for users to completely remove Trojan horse back door generic 15 BYNL as early as possible.2013年4月2日星期二
How to Delete Trojan horse Generic_r.AZB with Manual Removal Means
Is your computer attacked by Trojan horse Generic_r.AZB? Having tried several means on its removal but making no progress? This post and Tee Support online tech support team will help find the solution.
Trojan horse Generic_r.AZB Analysis
Trojan horse Generic_r.AZB is a variant from a huge Trojan clan that shares the same purpose and mechanism but it has minimal difference in affecting the target system. In most instances, the Trojan sneaks into the computer and completes the unauthorized installation through various security exploits. Following it will make several adjustments that is crucial to carry out its tasks. This malware is created to collect sensitive credentials and distribute other infection. A backdoor function is added to allow remote hackers to monitor the vulnerable system. Not only will the Trojan compromise your credit card, netbanking details, etc, but also the computer security system will be severely degraded until it becomes defenseless. Thus users should get rid of Trojan horse Generic_r.AZB once upon the detection. It's reported that Trojan horse Generic_r.AZB creates a new thread in Internet browsers like Internet Explorer, Mozilla Firefox, and Google Chrome. The Trojan influences these programs to activate itself once upon running the web browser. Besides, Trojan horse Generic_r.AZB can embed harmful code into Windows files and processes. By doing this, Trojan may initiate without being detected by antivirus program.Step by Step Remove Trojan horse Generic25.AAAS - Manual Removal Help
How much do you know about Trojan horse Generic25.AAAS virus? Why can't it be removed by security programs thoroughly? What's the best way to delete it once for all? It will be easily for you to walk through with Trojan horse Generic25.AAAS virus with this step-by-step guide. If you have any trouble with the removal process, please feel free to contact Tee Support agents 24/7 online for help.
Hot malware this week and removal tutorials:
How to Remove Strong Vault Online Backup?
http://blog.teesupport.com/how-to-uninstall-strong-vault-completely-remove-strong-vault-online-backup-manually/
How to Remove Qvo6.com Virus?
http://blog.teesupport.com/qvo6-com-virus-removal-guide-how-to-get-rid-of-qvo6-com-redirect-virus/
Trojan horse Generic25.AAAS Is an Undoubted Terrible Virus by Impression
- Trojan horse Generic25.AAAS is a nasty Trojan parasite
- Trojan horse Generic25.AAAS may show fake security & messages
- Trojan horse Generic25.AAAS may display numerous annoying advertisements
- Trojan horse Generic25.AAAS may come with additional spyware
- Trojan horse Generic25.AAAS violates your privacy and compromises your security
Basic Information about Trojan horse Generic25.AAAS
Trojan horse Generic25.AAAS is a regarded as an intractable computer virus that most of the antivirus software will not be supposed to pick it up readily. It is created to do favor for cyber criminals implementing evil things and trying to make computer invalid on work. While after Trojan horse Generic25.AAAS intrudes into computer furtively, a range of weird performance will be noticed on the vulnerable machine. The most evident change should the slowing down computer performance. It will drop computer with a variety of executable files, which are made use to degrade down the operation of program utility and consume system memory to lead computer to run weirdly. With the executable files, it also compulsively changes registry entries, turn off the real time protection, exploits system with security breach to bring computer with extra threats. What's crazy, the most important intention for the arrival of Trojan horse Generic25.AAAS is to gather your confidential information for online hackers to snatch illegal benefit. Other potential can be also caused to make your computer poor in work. Getting infected with this virus, you will be threatened to lose the important files or even the crash of operating system. Therefore, to carefully protect for the security of your machine, it is highly suggested to remove Trojan horse Generic25.AAAS from your computer as quickly as possible.Remove Trojan horse Generic25.AAAS Fast and Effectively
Currently, that users are always upsetting with Trojan horse Generic25.AAAS does not just attribute to antivirus software they use are not good. It is due to the fact that Trojan horse Generic25.AAAS hides deeply in registry entries with normal files’ names by mutating itself frequently that it is difficult to be picked up. What’s more, Trojan horse Generic25.AAAS can also affect the system files and block down your pc. Is there no solution with Trojan horse Generic25.AAAS? Of course not. Manual removal would be the best effective way to eliminate it. Now what are you waiting for? Just take steps as following:Manual Steps for Removing Trojan horse Generic25.AAAS Efficiently
Step 1: stop process on your system that related to Trojan horse Generic25.AAAS random.exe Step 2: Delete files that Trojan horse Generic25.AAAS has added to your system folders and files:%AppData%\Protector-[random].exe %appdata%\npswf32.dll %appdata%\Inspector-[rnd].exe %desktopdir%\ Trojan horse Generic25.AAAS.lnkStep 3: Remove registry entries that Trojan horse Generic25.AAAS has created to your system registry editor
HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Run “.exe” HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Run\ Trojan horse Generic25.AAAS HKCU\Software\Microsoft\Internet Explorer\Toolbar,LinksFolderName = C:\WINDOWS\Network Diagnostic\ HKEY_LOCAL_MACHINE\software\microsoft\windows\currentversion\explorer\shelliconoverlayidentifiers\(Note: if you are not expert in dealing with Trojan horse Generic25.AAAS 's files, processes, .dll files and registry entries, it may lead to mistakes damaging your system. If you want to get help from the expert, please feel free to start a live chat here.)
Hot malware this week and removal tutorials:
How to Remove Strong Vault Online Backup?
http://blog.teesupport.com/how-to-uninstall-strong-vault-completely-remove-strong-vault-online-backup-manually/
How to Remove Qvo6.com Virus?
http://blog.teesupport.com/qvo6-com-virus-removal-guide-how-to-get-rid-of-qvo6-com-redirect-virus/
Get Rid of Trojan horse SHeur4.AWYN Completely - Trojan horse SHeur4.AWYN Removal Help
Are you seriously mad with Trojan horse SHeur4.AWYN virus as it always turns up again after having it removed by security programs? What's the best solution to exterminate it permanently? If there is no solution to help you availably, this step-by-step guide will help remove Trojan horse SHeur4.AWYN easily. Once there is any problem during the removal process, please contact Tee Support agents 24/7 online for more detailed instructions with the expert.

What Way to Get Rid of Trojan horse SHeur4.AWYN Completely?
Currently, that users are always upsetting with Trojan horse SHeur4.AWYN does not just attribute to antivirus software they use are not good. It is due to the fact that Trojan horse SHeur4.AWYN hides deeply in registry entries with normal files’ names by mutating itself frequently that it is difficult to be picked up. What’s more, Trojan horse SHeur4.AWYN can also affect the system files and block down your pc. Is there no solution with Trojan horse SHeur4.AWYN? Of course not. Manual removal would be the best effective way to eliminate it. Now what are you waiting for? Just take steps as following:
The Lists of Symptoms about Trojan horse SHeur4.AWYN
- Trojan horse SHeur4.AWYN is a dangerous Trojan parasite
- Trojan horse SHeur4.AWYN may show fake security messages
- Trojan horse SHeur4.AWYN may display numerous annoying advertisements
- Trojan horse SHeur4.AWYN may be controlled by a remote person
- Trojan horse SHeur4.AWYN may come with additional spyware
- Trojan horse SHeur4.AWYN violates your privacy and compromises your security

Trojan horse SHeur4.AWYN Analysis
Trojan horse SHeur4.AWYN is an exceedingly obstinate virus that makes users painful to figure it out thoroughly no matter how many times they will try. According to the survey, this is a malevolent issue that particularly produced for gaining illegal benefit from the newbie by laying computer with kinds of destruction. Among the payloads, the most dangerous one is to keep track of your online activities and send the collected personal information to cyber criminals committing illegal profit. Apart from the above payload, it is also known as a tricky virus that keeps hiding the infected files into different locations with different files' names so as to prevent the deletion from antivirus software. To make system chaos in work, it will spread numerous executable codes in the vulnerable system to highly consume system memory, drag down operating system performance, mess up registry entries and dig system with security flaws for aiding other malware to intrude into computer smoothly. Under this circumstance, computer will get suffered from high level attack or even in vain to start up. Thus, for the sake of your computer's security, you are advised to get rid of Trojan horse SHeur4.AWYN immediately other than leaving it on system for a long time.What Way to Get Rid of Trojan horse SHeur4.AWYN Completely?
Currently, that users are always upsetting with Trojan horse SHeur4.AWYN does not just attribute to antivirus software they use are not good. It is due to the fact that Trojan horse SHeur4.AWYN hides deeply in registry entries with normal files’ names by mutating itself frequently that it is difficult to be picked up. What’s more, Trojan horse SHeur4.AWYN can also affect the system files and block down your pc. Is there no solution with Trojan horse SHeur4.AWYN? Of course not. Manual removal would be the best effective way to eliminate it. Now what are you waiting for? Just take steps as following:
Step-by-Step Instructions for Trojan horse SHeur4.AWYN Manual Removal
1. Find and stop Trojan horse SHeur4.AWYN running processes in the task manager. [random name].exe 2. All Trojan horse SHeur4.AWYN associated files listed below need to be removed:%UserProfile%\[random].exe %ProgramFiles%\Internet Explorer\Connection Wizard\[random] %Windir%\Microsoft.NET\Framework\[random].exe %System%\[random].exe %Temp%\[random].bat3.The related registry entries of Trojan horse SHeur4.AWYN to be deleted as listed below:
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Winlogon\[random] HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\policies\Explorer\Run\[random] HKEY_USERS\.DEFAULT\Software\Microsoft\Windows\CurrentVersion\Internet Settings\[random] HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\svflooje\Enum\[random](Note: if you are not expert in dealing with Trojan horse SHeur4.AWYN 's files, processes, .dll files and registry entries, it may lead to mistakes damaging your system. If you're confused about the process, don't be hesitated to get an instant help here.)
2013年3月24日星期日
Homepge Taken Over by websearch.just-browse.info? Remove Redirection Malware websearch.just-browse.info
Having websearch.just-browse.info installed but no idea how and when? Are you having a difficult time to get rid of this Internet homepage locker? This post and Tee Support online tech support team will help find the way out. Read more.
The modified homepage without your knowledge is a common sign of browser hijacker. What's more, users will find that no matter how many times you reset your homepage, it will open itself as websearch.just-browse.info once opening the affected web browser. It may seem to be a useful search program at first sight, but users may also smell the difference since Google or Yahoo won't display attracting ads language. Actually there are revenue-generating scheme that is running behind such browser virus and unseen by average computer users. It's also known as pay-per-click trick in which the cyber crooks gain a profit by sending traffic to client web sites. By forcefully replacing your default homepage with its own search page, websearch.just-browse.info also generates revenue for itself.
Most browser hijackers are installed as bundles and by the same methods as adware and PUPs( Potentially Unwanted Programs). Once completing the installation, this malware will separate from previous program and modifies host files and other settings to perform its tasks. Users may take notice of a couple of different interfaces of this search page with a different pictures below the search box. Except for the irrevocable search page and homepage, most users are complaining about the ads popups and unstable Internet browser even the whole system. Our research also shows that websearch.just-browse.info virus may downgrade security settings which may be exploited by other cyber bugs. Therefore we suggest users completely remove websearch.just-browse.info as early as possible.
websearch.just-browse.info Screenshots
Mos users find that it makes no difference to delete all tracking cookies, temp file and browsing history when it comes to websearch.just-browse.info uninsallation. To make things worse, the virus lingers but all diagnostic scans show up clean. All the difficulties are caused by the obscuration of modification which is hard for antivirus to trace with. In this case, manual removal is your preferred solution to deal with such undetectable threats. Having no idea as to how to start or worrying if make things worse? Please click here to read more about the detailed steps or click here to contact an online experts for further details.
What Is websearch.just-browse.info?
The modified homepage without your knowledge is a common sign of browser hijacker. What's more, users will find that no matter how many times you reset your homepage, it will open itself as websearch.just-browse.info once opening the affected web browser. It may seem to be a useful search program at first sight, but users may also smell the difference since Google or Yahoo won't display attracting ads language. Actually there are revenue-generating scheme that is running behind such browser virus and unseen by average computer users. It's also known as pay-per-click trick in which the cyber crooks gain a profit by sending traffic to client web sites. By forcefully replacing your default homepage with its own search page, websearch.just-browse.info also generates revenue for itself.
Most browser hijackers are installed as bundles and by the same methods as adware and PUPs( Potentially Unwanted Programs). Once completing the installation, this malware will separate from previous program and modifies host files and other settings to perform its tasks. Users may take notice of a couple of different interfaces of this search page with a different pictures below the search box. Except for the irrevocable search page and homepage, most users are complaining about the ads popups and unstable Internet browser even the whole system. Our research also shows that websearch.just-browse.info virus may downgrade security settings which may be exploited by other cyber bugs. Therefore we suggest users completely remove websearch.just-browse.info as early as possible.
websearch.just-browse.info Screenshots



Any Suggested Tool to Rid websearch.just-browse.info off?
Mos users find that it makes no difference to delete all tracking cookies, temp file and browsing history when it comes to websearch.just-browse.info uninsallation. To make things worse, the virus lingers but all diagnostic scans show up clean. All the difficulties are caused by the obscuration of modification which is hard for antivirus to trace with. In this case, manual removal is your preferred solution to deal with such undetectable threats. Having no idea as to how to start or worrying if make things worse? Please click here to read more about the detailed steps or click here to contact an online experts for further details.
Remove Trojan BackDoor.Generic15.COAQ - How to Delete BackDoor.Generic15.COAQ Threat?
BackDoor.Generic15.COAQ cannot be wiped out by AVG? Having gone through all other available approaches on its removal but none makes a difference? This post and Tee Support online tech support team will help find the solution.
 BackDoor.Generic15.COAQ is a backdoor Trojan detection that may result in multifacet harms to the target Windows computer.Users may not feel the difference at the initial phase, but that does not mean Trojan is hibernated and the computer is safe. With its backdoor function, author of this Trojan can connect to the target system from a remote place. Attackers can perform numerous malicious activities on the computer without getting user’s attention by sneakily establishing the communication with third parties.
BackDoor.Generic15.COAQ is found to monitor network traffic and steals user’s account. All collected data will be saved as log before sending out the distant server. This Backdoor Trojan may also prevent visits to certain websites, especially those for antivirus. On some instances, it's also the culprit that your Internet search queries are intermittently redirected to several irrelevant pages.
One of the major tasks is to monitor network traffic and gather sensitive data including banking account, FTP credentials and program log-in details and so on. Moreover the offensive and sophisticated mechanism of the backdoor is pretty destructiveness. Therefore users should completely remove BackDoor.Generic15.COAQ once upon the detection.
BackDoor.Generic15.COAQ is a backdoor Trojan detection that may result in multifacet harms to the target Windows computer.Users may not feel the difference at the initial phase, but that does not mean Trojan is hibernated and the computer is safe. With its backdoor function, author of this Trojan can connect to the target system from a remote place. Attackers can perform numerous malicious activities on the computer without getting user’s attention by sneakily establishing the communication with third parties.
BackDoor.Generic15.COAQ is found to monitor network traffic and steals user’s account. All collected data will be saved as log before sending out the distant server. This Backdoor Trojan may also prevent visits to certain websites, especially those for antivirus. On some instances, it's also the culprit that your Internet search queries are intermittently redirected to several irrelevant pages.
One of the major tasks is to monitor network traffic and gather sensitive data including banking account, FTP credentials and program log-in details and so on. Moreover the offensive and sophisticated mechanism of the backdoor is pretty destructiveness. Therefore users should completely remove BackDoor.Generic15.COAQ once upon the detection.
Step 1: Restart the infected computer into safe mode with networking by pressing and holding F8 before Windows launches.
Step 2: Search for and manually delete below files:
Step 3: Navigate to remove the registry entries associated as below in Registry Editor:
BackDoor.Generic15.COAQ Description
 BackDoor.Generic15.COAQ is a backdoor Trojan detection that may result in multifacet harms to the target Windows computer.Users may not feel the difference at the initial phase, but that does not mean Trojan is hibernated and the computer is safe. With its backdoor function, author of this Trojan can connect to the target system from a remote place. Attackers can perform numerous malicious activities on the computer without getting user’s attention by sneakily establishing the communication with third parties.
BackDoor.Generic15.COAQ is found to monitor network traffic and steals user’s account. All collected data will be saved as log before sending out the distant server. This Backdoor Trojan may also prevent visits to certain websites, especially those for antivirus. On some instances, it's also the culprit that your Internet search queries are intermittently redirected to several irrelevant pages.
One of the major tasks is to monitor network traffic and gather sensitive data including banking account, FTP credentials and program log-in details and so on. Moreover the offensive and sophisticated mechanism of the backdoor is pretty destructiveness. Therefore users should completely remove BackDoor.Generic15.COAQ once upon the detection.
BackDoor.Generic15.COAQ is a backdoor Trojan detection that may result in multifacet harms to the target Windows computer.Users may not feel the difference at the initial phase, but that does not mean Trojan is hibernated and the computer is safe. With its backdoor function, author of this Trojan can connect to the target system from a remote place. Attackers can perform numerous malicious activities on the computer without getting user’s attention by sneakily establishing the communication with third parties.
BackDoor.Generic15.COAQ is found to monitor network traffic and steals user’s account. All collected data will be saved as log before sending out the distant server. This Backdoor Trojan may also prevent visits to certain websites, especially those for antivirus. On some instances, it's also the culprit that your Internet search queries are intermittently redirected to several irrelevant pages.
One of the major tasks is to monitor network traffic and gather sensitive data including banking account, FTP credentials and program log-in details and so on. Moreover the offensive and sophisticated mechanism of the backdoor is pretty destructiveness. Therefore users should completely remove BackDoor.Generic15.COAQ once upon the detection.
BackDoor.Generic15.COAQ Removal Comments
As mentioned above, the Trojan may block visits to the websites where you may get antivirus update or installed. What's more, the Trojan itself uses developed hiding tactics to drop its files in Windows folder and renames them after legit program. Besides, the remote server may help keep itself up-to-date and repaired timely. If this is the case, you can follow below steps as reference to manually remove BackDoor.Generic15.COAQ:Step 1: Restart the infected computer into safe mode with networking by pressing and holding F8 before Windows launches.
Step 2: Search for and manually delete below files:
C:\WINDOWS\trlrokgq C:\WINDOWS\mjulinav.dll %AppData%\Bifrost\server.exe %ProgramFiles%\random.exe %LocalAppData%\ %LocalAppData%\.exe %AppData%\Microsoft\Windows\Templates\
Step 3: Navigate to remove the registry entries associated as below in Registry Editor:
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\Current Version\Run\random.exe" HKEY_CURRENT_USER\Software\Microsoft\CurrentVersion\Run\”MSN” = “%Temp%\34542.exe” HKEY_CURRENT_USER\AppEvents\Schemes\Apps\Explorer\Navigating HKEY_LOCAL_MACHINE\SOFTWARE\Classes\Interface\[random numbers] HKEY_CURRENT_USER\Software\Classes\.exe "(Default)" = 'ah' HKEY_CURRENT_USER\Software\Classes\.exe\shell\open\command "(Default)" = "%LocalAppData%\.exe" -a "%1" %*Notes: If you are still confused with above procedures, please click here to contact a 24/7 online expert for more details.
How to Remove Win32:Dropper-gen (Drp) Efficiently - Step by Step Removal Guide
Are you annoying in finding good way to get Win32:Dropper-gen (Drp) virus removed completely? How to fix it quickly and completely before it makes any severe damage on your computer? You can give a shot on the removal process as below. If you are still confused with the process, please feel free to contact Tee Support agents 24/7 online for further detailed instructions.
2. Press Ctrl+Alt+Del keys together to open the Windows Task Manager to stop the processes related to Win32:Dropper-gen (Drp).
[random name].exe
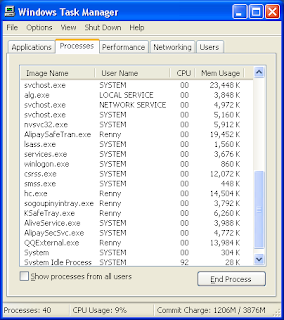
3. Show up Folder Options from Control Panel. Check the box of "Show hidden files and folders" and uncheck "Hide protected operating system files (Recommended)", then click "OK".
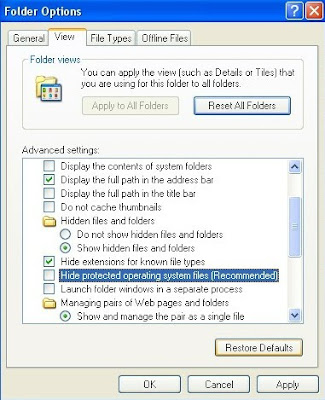
4. The related registry entries of Win32:Dropper-gen (Drp) to be deleted as listed below:
(Note: if you are not expert in dealing with Win32:Dropper-gen (Drp) 's files, processes, .dll files and registry entries, it may lead to mistakes damaging your system. If you want to get help from the expert, please feel free to start a live chat here.)
Basic Information about Win32:Dropper-gen (Drp)
Win32:Dropper-gen (Drp) is a notorious Trojan horse which is made to bring computer with diverse annoyance. Though AVG is the famous antivirus program which has the ability to detect the virus, it is regrettable that the security software has no ability to completely wipe up the pieces of Win32:Dropper-gen (Drp) thoroughly. According to the research by technical experts, Win32:Dropper-gen (Drp) is regarded to scatter numerous infected files into different parts of system locations to bypass itself from the complete deletion by antivirus software. With the help of executable files, it is capable to silently spend out your memory resources, stop system programs, pop up advertisements and slow down computer performance and Internet speed as well. Everything just seems like to perform weirdly and sluggishly. What's worse, if it won't be exterminated in time, you may even get redirected to malicious websites which are hosted by cyber criminals to insert computer with extra infections for causing further severe detriment. Needless to say, as Win32:Dropper-gen (Drp) contains with bunches of dangers that users should eradicate it as quickly as possible.General Traits about Win32:Dropper-gen (Drp) Virus
- Win32:Dropper-gen (Drp) is a dangerous Trojan parasite
- Win32:Dropper-gen (Drp) may display numerous annoying advertisements
- Win32:Dropper-gen (Drp) may come with additional spyware
- Win32:Dropper-gen (Drp) violates your privacy and compromises your security
Effective Way to Eliminate Win32:Dropper-gen (Drp) Safely
Many users may have tried a variety of ways to get rid of Win32:Dropper-gen (Drp) but fall on stony ground. To be frank, since virus in fast-mutating, there is no antivirus software can solve because it takes time for antivirus software to keep trace with virus. And you may also do "regedit" in the Run command box, but all failed. Fortunately, manual removal is to be the most effective way to remove Win32:Dropper-gen (Drp). Here is the step-by-step guide for removal.Guide to Delete Win32:Dropper-gen (Drp) Manually and Availably
1. Restart your computer into safe mode with networking by pressing F8 key constantly before the Windows starts to launch.
2. Press Ctrl+Alt+Del keys together to open the Windows Task Manager to stop the processes related to Win32:Dropper-gen (Drp).
[random name].exe

3. Show up Folder Options from Control Panel. Check the box of "Show hidden files and folders" and uncheck "Hide protected operating system files (Recommended)", then click "OK".

4. The related registry entries of Win32:Dropper-gen (Drp) to be deleted as listed below:
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Winlogon\[random] HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\policies\Explorer\Run\[random] HKEY_USERS\.DEFAULT\Software\Microsoft\Windows\CurrentVersion\Internet Settings\[random] HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\svflooje\Enum\[random]
(Note: if you are not expert in dealing with Win32:Dropper-gen (Drp) 's files, processes, .dll files and registry entries, it may lead to mistakes damaging your system. If you want to get help from the expert, please feel free to start a live chat here.)
Remove Vista Home Security 2013 - How to Uninstall Vista Home Security 2013 Malware Completely?
Are you looking around to find an effective way to fix Vista Home Security 2013 virus? Why can’t it be stop by antivirus programs efficiently? What’s the fastest and easiest way to get rid of it completely? You can give a shot on the removal process as below. If you are still confused with the process, please feel free to contact Tee Support agents 24/7 online for further detailed instructions.

How Can Vista Home Security 2013 Install into Computer Stealthily?
Vista Home Security 2013 is a bogus program that specially created to extort money from the victims by scaring them with bunches of infections. For the most cases that computers get infected with this program can be attributed to the distribution of Trojan horses. Besides, it can also get into computer via the help of spam email attachment or other unknown freeware. Thus, users need to be highly cautious for the online activities. To safely defend for the security of your PC, you are suggested to remove the useless fake program of Vista Home Security 2013 as fast as possible.

2. Find and stop Vista Home Security 2013 running processes in the task manager. [random name].exe

3. All Vista Home Security 2013 associated files listed below need to be removed:
(Note: no sufficient expertise in dealing with Vista Home Security 2013 's files, processes, .dll files and registry entries may lead to mistakes damaging your system. If you are not familiar with the removal guide, please start a live chat with expert here.)
Lear about Vista Home Security 2013
Vista Home Security 2013 is a notorious fake anti-virus program which does the harmful damages on the targeted computers similar to other rogue programs such as Vista Home Security Plus 2013 and Vista Home Security Pro 2013. Without any difference, they are all produced by cyber criminals for ripping money off from your affected machine by utilizing deceitful trick. Once installed, a pop-up window which carries with security alert message will be initiated by Vista Home Security 2013 to cheat the innocents to start a scan for system files by just clicking on the window. If you are clicking on the window unsuspectingly, you will be shown with a list of security alerts and infections. By showing the larger number of threats, it is planning to make you seriously worry about the security of your computer so that it can take the chance to deceive users into paying money for its so-called full product to wipe up all the infections for you. Indeed, as you may realize, there is not threats on your computer at all. They are existed for the purpose to lure money from your account.
How Can Vista Home Security 2013 Install into Computer Stealthily?
Vista Home Security 2013 is a bogus program that specially created to extort money from the victims by scaring them with bunches of infections. For the most cases that computers get infected with this program can be attributed to the distribution of Trojan horses. Besides, it can also get into computer via the help of spam email attachment or other unknown freeware. Thus, users need to be highly cautious for the online activities. To safely defend for the security of your PC, you are suggested to remove the useless fake program of Vista Home Security 2013 as fast as possible.
Vista Home Security 2013 is Regarded as Big Threat by Impressions
- Vista Home Security 2013 is a malicious fake antispyware program
- Vista Home Security 2013 may spread via Trojans
- Vista Home Security 2013 may display numerous fake security messages
- Vista Home Security 2013 may install additional spyware to your computer
- Vista Home Security 2013 violates your privacy and compromises your security
- Vista Home Security 2013 causes your computer slowing down and even crashing constantly
How to Eliminate Vista Home Security 2013 out from Your Computer Manually?
Currently, that users are always upsetting with Vista Home Security 2013 does not just attribute to antivirus software they use are not good. It is due to the fact that Vista Home Security 2013 hides deeply in registry entries with normal files’ names by mutating itself frequently that it is difficult to be picked up. What’s more, Vista Home Security 2013 can also affect the system files and block down your pc. Is there no solution with Vista Home Security 2013? Of course not! Manual removal would be the best effective way to eliminate it. Now what are you waiting for? Just take steps as following:Step-by-Step Manual Removal Guide for Vista Home Security 2013
1. Restart your computer into safe mode with networking by pressing F8 key constantly before the Windows starts to launch.
2. Find and stop Vista Home Security 2013 running processes in the task manager. [random name].exe

3. All Vista Home Security 2013 associated files listed below need to be removed:
%UserProfile%\[random].exe %ProgramFiles%\Internet Explorer\Connection Wizard\[random] %Windir%\Microsoft.NET\Framework\[random].exe %System%\[random].exe %Temp%\[random].bat
4. The related registry entries of Vista Home Security 2013 to be deleted as listed below:
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Winlogon\[random] HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\policies\Explorer\Run\[random] HKEY_USERS\.DEFAULT\Software\Microsoft\Windows\CurrentVersion\Internet Settings\[random] HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\svflooje\Enum\[random]
(Note: no sufficient expertise in dealing with Vista Home Security 2013 's files, processes, .dll files and registry entries may lead to mistakes damaging your system. If you are not familiar with the removal guide, please start a live chat with expert here.)
Remove Api.mybrowserbar.com From IE, Firefox and Google Chrome
Don't know how to get your Google search page back with the fake Api.mybrowserbar.com once? Having tried several tools on its removal but without any luck? If you were experiencing that now and googling a qualified tool, this post and Tee Support researchers will help find the way out.

Step 1: Restart the infected computer into safe mode with networking by pressing and holding F8 before Windows launches.
Step 2: Search for and manually delete below files:
Api.mybrowserbar.com Virus Introduction
Api.mybrowserbar.com is a browser hijacker that transforms your homepage into its own customized one which seems to be enhanced by Yahoo search, one of the most popular search engine. Other than a search page, the supportive adware also encompasses a browser toolbar which consists of various buttons. The toolbar may look useful at first sight, however, there are reports that some of the buttons may point your search to malicious or advertising pages just as the search engine of Api.mybrowserbar.com. With regard to Api.mybrowserbar.com itself, even created with a sound and compact search box, many computer users are objecting its presence since the algorithm are obviously skeptical. They also complain about the changes it makes to the system without consent, especially those on the target browser. You may find below symptoms:- Api.mybrowserbar.com replaces your default homepage search page.
- Adds suspicious links to bookmark files and favorites.
- Unresponsive script errors keeps popping up on certain pages.
- The infected browser becomes easily frozen and crashed.
- Extra icons are added on desktop which is linked with ads pages.
- System is severely slowed down with high CPU consumption.
Api.mybrowserbar.com Screenshot

Api.mybrowserbar.com Installation & Removal
Api.mybrowserbar.com generally comes bundled with unknown programs that you may download when visiting web site that offers free videos or file downloads. It drops the harmless file in Windows system folder once completing the installation. Users find that it makes no difference to manually check host file and empty browsing history.What's more, the virus haunts while all scanners show an absolute clean system. Right now manual means is your preferred solution to eliminate Api.mybrowserbar.com browser hijacker. Below is the details on how:Step 1: Restart the infected computer into safe mode with networking by pressing and holding F8 before Windows launches.
Step 2: Search for and manually delete below files:
%System%\winlogin.exe %Windir%\winrun.exeStep 3: Navigate to remove the registry entries associated as below in Registry Editor:
HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\Main\CustomizeSearch=[site address] HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\Main\Search Bar=[site address] HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\LowRegistry\DontShowMeThisDialogAgain HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\[random] HKEY_CURRENT_USER\Software\Microsoft\Windows NT\CurrentVersion\Winlogon\Shell =[random].exe
Notes: If you are still confused with above procedures, please click here to contact a 24/7 online expert for more details.
How to Remove Trojan horse BackDoor.Generic16.AAEZ Virus - Manual Removal Tips
Trojan horse BackDoor.Generic16.AAEZ has been reported by antivirus software? Has spent lots of time to get rid of it but still invalid? You can give a shot on the removal process as below. If you are still confused with the process, please feel free to contact Tee Support agents 24/7 online for further detailed instructions.

2.The associated files of Trojan horse BackDoor.Generic16.AAEZ to be deleted are listed below:
Analysis of Trojan horse BackDoor.Generic16.AAEZ
Trojan horse BackDoor.Generic16.AAEZ is detected as a vicious Trojan virus comes from the big infamous Generic family which has brought computers with great troubles by hundreds of harmful variants. Under most of the circumstances, there is not an antivirus program which can be used to meet with the help to get rid of Trojan horse BackDoor.Generic16.AAEZ completely. Whenever you restart your computer, it can be detected again. As a malicious computer infection, there will be numerous damages to lay on your system to degrade down computer performance as well as other invasion defense. Normally, Trojan horse BackDoor.Generic16.AAEZ is able to insert computer with infected files to make operating system fail to respond quickly with the executable files that it implants. Besides, it is also blamed to change system settings, mess up registry entries, overwrite MBR, stop system processes or open backdoor in the background of system to result computer even vulnerable for other online threats. The last but not the least, it is possible for the virus giving unauthorized access for remote hackers sneaking into computer to steal your confidential information away. Anyway, to safely protect for your computer, Trojan horse BackDoor.Generic16.AAEZ should be removed thoroughly from your machine as soon as possible.Trojan horse BackDoor.Generic16.AAEZ Considered as a Threatening Trojan by Impressions
- Trojan horse BackDoor.Generic16.AAEZ is a nasty Trojan parasite
- Trojan horse BackDoor.Generic16.AAEZ may show fake error messages
- Trojan horse BackDoor.Generic16.AAEZ may display numerous annoying advertisements
- Trojan horse BackDoor.Generic16.AAEZ may be controlled by a remote person
- Trojan horse BackDoor.Generic16.AAEZ may come with additional spyware
- Trojan horse BackDoor.Generic16.AAEZ violates your privacy and compromises your security
Effective Way to Eliminate Trojan horse BackDoor.Generic16.AAEZ Safely
Many users may have tried a variety of ways to get rid of Trojan horse BackDoor.Generic16.AAEZ but fall on stony ground. To be frank, since virus in fast-mutating, there is no antivirus software can solve because it takes time for antivirus software to keep trace with virus. And you may also do "regedit" in the Run command box, but all failed. Fortunately, manual removal is to be the most effective way to remove Trojan horse BackDoor.Generic16.AAEZ. Here is the step-by-step guide for removal.Manual Removal Instruction for Trojan horse BackDoor.Generic16.AAEZ
1. Press Ctrl+Alt+Del keys together to open the Windows Task Manager to stop the processes related to Trojan horse BackDoor.Generic16.AAEZ. [random name].exe
2.The associated files of Trojan horse BackDoor.Generic16.AAEZ to be deleted are listed below:
%AllUsersProfile%\{random}
C:\WINDOWS\System64/32\svchost.exe
%AllUsersProfile%\Application Data\.dll
%AllUsersProfile%\Application Data\.exe
3. The related registry entries of Trojan horse BackDoor.Generic16.AAEZ to be deleted as listed below:
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Winlogon\[random] HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\policies\Explorer\Run\[random] HKEY_USERS\.DEFAULT\Software\Microsoft\Windows\CurrentVersion\Internet Settings\[random] HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\svflooje\Enum\[random]
(Note: if you have no sufficient expertise in dealing with Trojan horse BackDoor.Generic16.AAEZ 's files, processes, .dll files and registry entries, it may lead to mistakes damaging your system, so please be careful during the manual removal operation. If you are not familiar with the processes, please feel free to start a live chat here.)
How to Remove abuchak.net Redirect Virus - Abuchak Search Removal Guide
Find it's hard to get the appropriate webpage due to abuchak.net reidirection? Having gone through all troubleshooting steps but it makes no difference? This post and Tee Support lab researchers will walk you through such mess around the first time.

For Firefox: Clik the "Firefox" button in the upper left of Firefox browser menu and then hit “Options" The Options window will appear; Select the "Advanced" tab; Click the “network”tab and then the “settings”button; Checkmark option“No Proxy”; Click “OK” and then “OK” again to disable proxy settings.
For Google Chrome: Open Google Chrome ; Go to the key at the top right, then “Options”->”Advanced”; Click “Change proxy settings” located in “Network”; Click “Connections” tab; Click “LAN Settings”; Checkmark “Do not activate a proxy server”.
For Internet Explorer: Open Internet Explorer; Click Tools; Click on Internet Options; In the Internet Options window click "Connections tab", Then click on the LAN settings button" Uncheck the check box labeled “Use a proxy server for your LAN” under the Proxy Server section and press "OK".
Step 2- Remove these associated Files on your hard drive such as:
abuchak.net Information
abuchak.net is reported to be a nasty Google redirect virus that are crafted to profit from pay-per-click traffic. This page is highlighted with a search box, making itself a real search engine. Users may find that the search results given by Abuchak are all ads-serving, instead of the expected informative links. As a sophisticated browser hijacker, Abuchak not only greatly disturbs web browser functionality, but also causes damage to the whole system. abuchak.net is commonly downloaded as a bundled program of multimedia players and web utilities. Installing this tool also loads Abuchak in the background when users unwittingly download such free application. You will see the changes once upon the installation since it modifies DNS settings to redirect your search queries to abuchak.net and other sponsored websites, taking ecostartpage.com as an example. Users may find that both the search commands via the search engine or URL bar are both redirected to irrelevant pages. On the other hand, the infected Infected Internet Explorer, Firefox or Google Chrome become crispy, especially when there are a little more tabs are opened or playing games. Many users find that there are multiple serious complications with a redirection symptom. Some may suffer from annoying popups, some are unable to run Windows update or complete the system scanning with an antivirus. Others may complain about the disappearing desktop icons or blockage of visit to certain websites, mainly for antivirus or netbanking.abuchak.net Screenshot

Any Suggested Tool to Completely Remove abuchak.net?
Most users will find them hard to remove after deleting all tracking cookies, temp file and browsing history. To make things worse, the redirection stays on even though all diagnostic scans show nothing abnormal. All the difficulties is caused by the obscuration of modification which is hard for antivirus to trace with.In such cases, manual removal is suggested to get rid of abuchak.net redirect virus.Referential Steps to Manually Remove Abuchak Malware
Step 1: Disable Proxy:%AllUsersProfile%{random}
%AllUsersProfile%{random}*.lnk
Step 3: Navigate to remove the registry entries associated as below in Registry Editor:
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\Current Version\Run\random.exe" HKEY_CURRENT_USER\Software\Microsoft\CurrentVersion\Run\”MSN” = “%Temp%\34542.exe” HKEY_CURRENT_USER\AppEvents\Schemes\Apps\Explorer\Navigating HKEY_LOCAL_MACHINE\SOFTWARE\Classes\Interface\[random numbers] HKEY_CURRENT_USER\Software\Classes\.exe "(Default)" = 'ah' HKEY_CURRENT_USER\Software\Classes\.exe\shell\open\command "(Default)" = "%LocalAppData%\.exe" -a "%1" %*Notes: If you are still confused with above procedures, please click here to contact a 24/7 online expert for more details.
2013年3月15日星期五
How to Remove Trojan.Win32.Hosts2.gen Virus? Complete Trojan.Win32.Hosts2.gen Removal
Trojan.Win32.Hosts2.gen Virus is a serious Trojan and your PC will not be secure until Trojan.Win32.Hosts2.gen Virus is removed. However, Trojan.Win32.Hosts2.gen Virus cannot be removed like a regular application can. It is nowhere to be found among the apps listed on Add/Remove panel and it does not allow you to use any anti-virus Antivirus to remove it.
The best way to get rid of Trojan.Win32.Hosts2.gen Virus is to check your registry and disks and manually remove Trojan.Win32.Hosts2.gen Virus to fix your PC. We are providing you with that sort of a tutorial (please take a backup of Windows Registry before starting the process).
Expert Recommendation: Your manual removal of Trojan.Win32.Hosts2.gen Virus is at your own risk. We strictly restrict you take caution that any improper operation can permanently damage your system. If you still worried about the removal of Trojan.Win32.Hosts2.gen Virus, you can get some professional help from the trusted and reliable Online Technical Support!
The best way to get rid of Trojan.Win32.Hosts2.gen Virus is to check your registry and disks and manually remove Trojan.Win32.Hosts2.gen Virus to fix your PC. We are providing you with that sort of a tutorial (please take a backup of Windows Registry before starting the process).
Expert Recommendation: Your manual removal of Trojan.Win32.Hosts2.gen Virus is at your own risk. We strictly restrict you take caution that any improper operation can permanently damage your system. If you still worried about the removal of Trojan.Win32.Hosts2.gen Virus, you can get some professional help from the trusted and reliable Online Technical Support!
Adware Generic5.RQV Cannot Be Removed By AVG
AVG detected Adware Generic5.RQV but cannot remove it? Having tried several tools but none is able to fix the issue? This post and Tee Support online tech support team will help find the ideal solution.
 Adware Generic5.RQV is detected as an adware created to display numerous popup ads or adverting links to certain ads pages on the target system. Users may find that the system is flooded with unwanted ads most of which are prompting you to download or purchase some product. Actually such adware can record your browsing history and bombard the browser accordingly with the ads. It may leave serious side effects on the target web browser of Internet Explorer, Firefox and Google Chrome. Except by inserting extensions and plug-ins, the adware may also transform your default search page and redirect your search queries to irrelevant dubious website, among which some may be malicious too. Adware Generic5.RQV keeps track of your online activities and installs other malware on the vulnerable Window computer, steals the users' personal data and information and sends them to a remote server. Therefore users should get rid of Adware Generic5.RQV the first time around.
Adware Generic5.RQV is detected as an adware created to display numerous popup ads or adverting links to certain ads pages on the target system. Users may find that the system is flooded with unwanted ads most of which are prompting you to download or purchase some product. Actually such adware can record your browsing history and bombard the browser accordingly with the ads. It may leave serious side effects on the target web browser of Internet Explorer, Firefox and Google Chrome. Except by inserting extensions and plug-ins, the adware may also transform your default search page and redirect your search queries to irrelevant dubious website, among which some may be malicious too. Adware Generic5.RQV keeps track of your online activities and installs other malware on the vulnerable Window computer, steals the users' personal data and information and sends them to a remote server. Therefore users should get rid of Adware Generic5.RQV the first time around.
Step 1: Restart the infected computer into safe mode with networking by pressing and holding F8 before Windows launches.
Step 2: Search for and manually delete below files:
What Is Adware Generic5.RQV?
 Adware Generic5.RQV is detected as an adware created to display numerous popup ads or adverting links to certain ads pages on the target system. Users may find that the system is flooded with unwanted ads most of which are prompting you to download or purchase some product. Actually such adware can record your browsing history and bombard the browser accordingly with the ads. It may leave serious side effects on the target web browser of Internet Explorer, Firefox and Google Chrome. Except by inserting extensions and plug-ins, the adware may also transform your default search page and redirect your search queries to irrelevant dubious website, among which some may be malicious too. Adware Generic5.RQV keeps track of your online activities and installs other malware on the vulnerable Window computer, steals the users' personal data and information and sends them to a remote server. Therefore users should get rid of Adware Generic5.RQV the first time around.
Adware Generic5.RQV is detected as an adware created to display numerous popup ads or adverting links to certain ads pages on the target system. Users may find that the system is flooded with unwanted ads most of which are prompting you to download or purchase some product. Actually such adware can record your browsing history and bombard the browser accordingly with the ads. It may leave serious side effects on the target web browser of Internet Explorer, Firefox and Google Chrome. Except by inserting extensions and plug-ins, the adware may also transform your default search page and redirect your search queries to irrelevant dubious website, among which some may be malicious too. Adware Generic5.RQV keeps track of your online activities and installs other malware on the vulnerable Window computer, steals the users' personal data and information and sends them to a remote server. Therefore users should get rid of Adware Generic5.RQV the first time around.
Possible Symptoms of Adware Generic5.RQV Infection
- Automatically opened new tabs which display advertisements.
- Redirects of Internet search queries to unknown web sites.
- Modified homepage which cannot change it back by resetting.
- Blocked visit to legitimate security web sites with error prompts.
- Unresponsive script error boxes asking to continue or stop.
- Crashed web browser when there is too many tabs opened.
How to Remove Adware Generic5.RQV?
Adware Generic5.RQV is commonly spread by packing with other free programs that are offered on most multimedia pages. Users should keep an eye on downloadable programs such as games, browser plug-ins or tools. If you cannot remove Adware Generic5.RQV with a security tool, we have outlined a simple to follow instructions on this page which you can follow as reference:Step 1: Restart the infected computer into safe mode with networking by pressing and holding F8 before Windows launches.
Step 2: Search for and manually delete below files:
%Documents and Settings%\All Users\Application Data\[random]\ %Documents and Settings%\All Users\Application Data\[random]\[random].exe %Documents and Settings%\All Users\Application Data\[random]\[random].mofStep 3: Navigate to remove the registry entries associated as below in Registry Editor which cannot be opened via regedit command:
HKEY_CLASSES_ROOT\PersonalSS.DocHostUIHandler HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\Download “RunInvalidSignatures” = “1″ HKEY_LOCAL_MACHINESOFTWAREClasses[trojan name]IEHelper.DNSGuardCurVer HKEY_LOCAL_MACHINESOFTWAREClasses[trojan name]IEHelper.DNSGuardCLSID HKEY_LOCAL_MACHINESOFTWAREClasses[trojan name]IEHelper.DNSGuard HKEY_LOCAL_MACHINESOFTWAREClasses[trojan name]IEHelper.DNSGuard.1 HKEY_LOCAL_MACHINESOFTWAREMicrosoftInternet ExplorerToolbar “[trojan name]”Notes: If you are still confused with above procedures, please click here to contact a 24/7 online expert for more details.
Best Way to Remove PWSteal.Frethog Completely - Manual Removal Guide
Have you found a straightforward way to get PWSteal.Frethog virus removed directly? If not, how can it be removed completely without return back again? You can give a shot on the removal process as below. If you are still confused with the process, please feel free to contact Tee Support agents 24/7 online for further detailed instructions.
 PWSteal.Frethog is found as a high level dangerous Trojan horse which serves for cyber criminals for doing vicious damages on user’s computer. Generally, this is not a virus which can spread on its own but always with distribution of spam email attachment, free program downloads or malicious advertisements. To prevent it from downloading into computer, users need to watch out for online activities.
When it is in, PWSteal.Frethog will drop system with a number of infected files which can be hardly found by users as they have been mutated into the form of system files such .dll and .exe. It is aimed to bypass the deletion of antivirus software to allow its long existence on your computer to add lots of attack. It is capable to mess up the essential part of system such as Task Manager, registry entries and MBR (Master boot Record) to prevent programs from running efficiently. In other words, computer performance and the network speed will be largely degraded down. You can be also redirected constantly by the browser hijacker that it brings into your PC to unexpected links to upset you badly. All of the malicious harmful characteristics are all designed by its creator cyber criminal to try to gain your personal information for doing illegal activities. Thus, users shouldn’t keep such highly offensive virus on your computer for long. To the opposite, it is urgent to get rid of PWSteal.Frethog at once without any delay.
PWSteal.Frethog is found as a high level dangerous Trojan horse which serves for cyber criminals for doing vicious damages on user’s computer. Generally, this is not a virus which can spread on its own but always with distribution of spam email attachment, free program downloads or malicious advertisements. To prevent it from downloading into computer, users need to watch out for online activities.
When it is in, PWSteal.Frethog will drop system with a number of infected files which can be hardly found by users as they have been mutated into the form of system files such .dll and .exe. It is aimed to bypass the deletion of antivirus software to allow its long existence on your computer to add lots of attack. It is capable to mess up the essential part of system such as Task Manager, registry entries and MBR (Master boot Record) to prevent programs from running efficiently. In other words, computer performance and the network speed will be largely degraded down. You can be also redirected constantly by the browser hijacker that it brings into your PC to unexpected links to upset you badly. All of the malicious harmful characteristics are all designed by its creator cyber criminal to try to gain your personal information for doing illegal activities. Thus, users shouldn’t keep such highly offensive virus on your computer for long. To the opposite, it is urgent to get rid of PWSteal.Frethog at once without any delay.
Learn about PWSteal.Frethog
 PWSteal.Frethog is found as a high level dangerous Trojan horse which serves for cyber criminals for doing vicious damages on user’s computer. Generally, this is not a virus which can spread on its own but always with distribution of spam email attachment, free program downloads or malicious advertisements. To prevent it from downloading into computer, users need to watch out for online activities.
When it is in, PWSteal.Frethog will drop system with a number of infected files which can be hardly found by users as they have been mutated into the form of system files such .dll and .exe. It is aimed to bypass the deletion of antivirus software to allow its long existence on your computer to add lots of attack. It is capable to mess up the essential part of system such as Task Manager, registry entries and MBR (Master boot Record) to prevent programs from running efficiently. In other words, computer performance and the network speed will be largely degraded down. You can be also redirected constantly by the browser hijacker that it brings into your PC to unexpected links to upset you badly. All of the malicious harmful characteristics are all designed by its creator cyber criminal to try to gain your personal information for doing illegal activities. Thus, users shouldn’t keep such highly offensive virus on your computer for long. To the opposite, it is urgent to get rid of PWSteal.Frethog at once without any delay.
PWSteal.Frethog is found as a high level dangerous Trojan horse which serves for cyber criminals for doing vicious damages on user’s computer. Generally, this is not a virus which can spread on its own but always with distribution of spam email attachment, free program downloads or malicious advertisements. To prevent it from downloading into computer, users need to watch out for online activities.
When it is in, PWSteal.Frethog will drop system with a number of infected files which can be hardly found by users as they have been mutated into the form of system files such .dll and .exe. It is aimed to bypass the deletion of antivirus software to allow its long existence on your computer to add lots of attack. It is capable to mess up the essential part of system such as Task Manager, registry entries and MBR (Master boot Record) to prevent programs from running efficiently. In other words, computer performance and the network speed will be largely degraded down. You can be also redirected constantly by the browser hijacker that it brings into your PC to unexpected links to upset you badly. All of the malicious harmful characteristics are all designed by its creator cyber criminal to try to gain your personal information for doing illegal activities. Thus, users shouldn’t keep such highly offensive virus on your computer for long. To the opposite, it is urgent to get rid of PWSteal.Frethog at once without any delay.
What are the symptoms showing on PWSteal.Frethog?
- PWSteal.Frethog is a nasty Trojan parasite
- PWSteal.Frethog may show fake security & messages
- PWSteal.Frethog may display numerous annoying advertisements
- PWSteal.Frethog may be controlled by a remote person
- PWSteal.Frethog may come with additional spyware
- PWSteal.Frethog violates your privacy and compromises your security
Effective Way to Get Rid of PWSteal.Frethog Virus:
Currently, that users are always upsetting with PWSteal.Frethog does not just attribute to antivirus software they use are not good. It is due to the fact that PWSteal.Frethog hides deeply in registry entries with normal files’ names by mutating itself frequently that it is difficult to be picked up. What’s more, PWSteal.Frethog can also affect the system files and block down your pc. Is there no solution with PWSteal.Frethog? Of course not. Manual removal would be the best effective way to eliminate it. Now what are you waiting for? Just take steps as following:Step-by-Step Manual Removal for PWSteal.Frethog
1. Find and stop PWSteal.Frethog running processes in the task manager. [random name].exe 2. All PWSteal.Frethog associated files listed below need to be removed:%UserProfile%\[random].exe %ProgramFiles%\Internet Explorer\Connection Wizard\[random] %Windir%\Microsoft.NET\Framework\[random].exe %System%\[random].exe %Temp%\[random].bat3.The related registry entries of PWSteal.Frethog to be deleted as listed below:
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Winlogon\[random] HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\policies\Explorer\Run\[random] HKEY_USERS\.DEFAULT\Software\Microsoft\Windows\CurrentVersion\Internet Settings\[random] HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\svflooje\Enum\[random](Note: if you are not expert in dealing with PWSteal.Frethog 's files, processes, .dll files and registry entries, it may lead to mistakes damaging your system. If you're confused about the process, you are welcome to ask questions with expert here.)
Trojan horse Agent4.PZF Removal Guides
Is your computer infected with Trojan horse Agent4.PZF and starting to act up? Having tried several means on its removal but going nowhere? So what kind of threats it may cause to the infected machine if I let it be? This post and Tee Support online tech support team will help find the way out around the first time.

Step 1: Restart the computer into safe mode with networking by pressing and holding F8 before Windows launches and selecting the needed mode with arrow keys.
Step 2: Search for and delete its related files in Local Disk C:
What Is Trojan horse Agent4.PZF?
Trojan horse Agent4.PZF is a member of the Trojan Agent family which are set with similar payloads when running on the computer. In most instances, users report that Trojan horse Agent4.PZF is interfering with Internet browsers like Internet Explorer, Mozilla Firefox, and Google Chrome by generating various popup ads on certain websites and unexpected redirect to websites that's totally unrelated.The Trojan will configure system registry in a way that it can be activated once Windows gets loaded. Additionally, various harmful files and process will hide inside the computer that are monitored by the Trojan to carry out its malicious tasks without being spotted. The main purpose of this malware is to collect sensitive information such as banking accounts, credit card details and FTP credentials, the computer IP and Windows type that is running on it, etc. All gathered data will be saved as log file before sending to remote server. In order to survive and expand the intrusion, the Trojan will also modify even jeopardize security services which in turn, the computer may become prone to other infection. Therefore users should take Trojan horse Agent4.PZF seriously and take steps to remove it once upon the detection.
Trojan horse Agent4.PZF Distribution and Installation
Cyber crooks deploy this threat which may sneaks into the system from spam email campaign, social networks, or risky web pages. The malware is installed without users knowledge and may lurk in the system for a while or burst as soon as it completes the installation. Therefore users may not see its symptoms except for the antivirus notification of the Trojan. You may find that the Trojan lingers at each restart even it's deleted according to last session. If this is the case, you can follow below manual removal steps to get rid of Trojan horse Agent4.PZF:Step 1: Restart the computer into safe mode with networking by pressing and holding F8 before Windows launches and selecting the needed mode with arrow keys.
Step 2: Search for and delete its related files in Local Disk C:
%appdata%\npswf32.dll
%appdata%\Inspector-{random}.exe
%desktopdir%\ Win32:sirefef-aoo [trj].lnk
Step 3: Navigate to remove the registry entries associated as below in Registry Editor:
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Run\{random characers}.exe
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\RunOnce\{random characers}.exe
HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Run\{random characers}.exe
HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Run "[random].exe"
HKEY_LOCAL_MACHINE\SOFTWARE\Classes\Interface\[random numbers]
HKEY_CURRENT_USER\Software\Microsoft\Windows NT\CurrentVersion\Winlogon\Shell = [random]
Notes: If you are still confused with above procedures, please click here to contact a 24/7 online expert for more details.
订阅:
博文 (Atom)




